Protecting your online accounts is more crucial than ever, especially with the rise of cybersecurity threats. A simple password is no longer enough to keep your information secure.
However, two-factor authentication (2FA) offers an added layer of security, ensuring that your accounts are safeguarded even if your password is compromised. This article will guide you through enabling 2FA on Short.io and exploring its benefits.
How to Enable 2-Factor Authentication on Short.io
Enhancing your account security on Short.io is a breeze with 2FA. Follow these simple steps to enable 2FA using an authenticator app like Google Authenticator.
- Log into Your Short.io Account
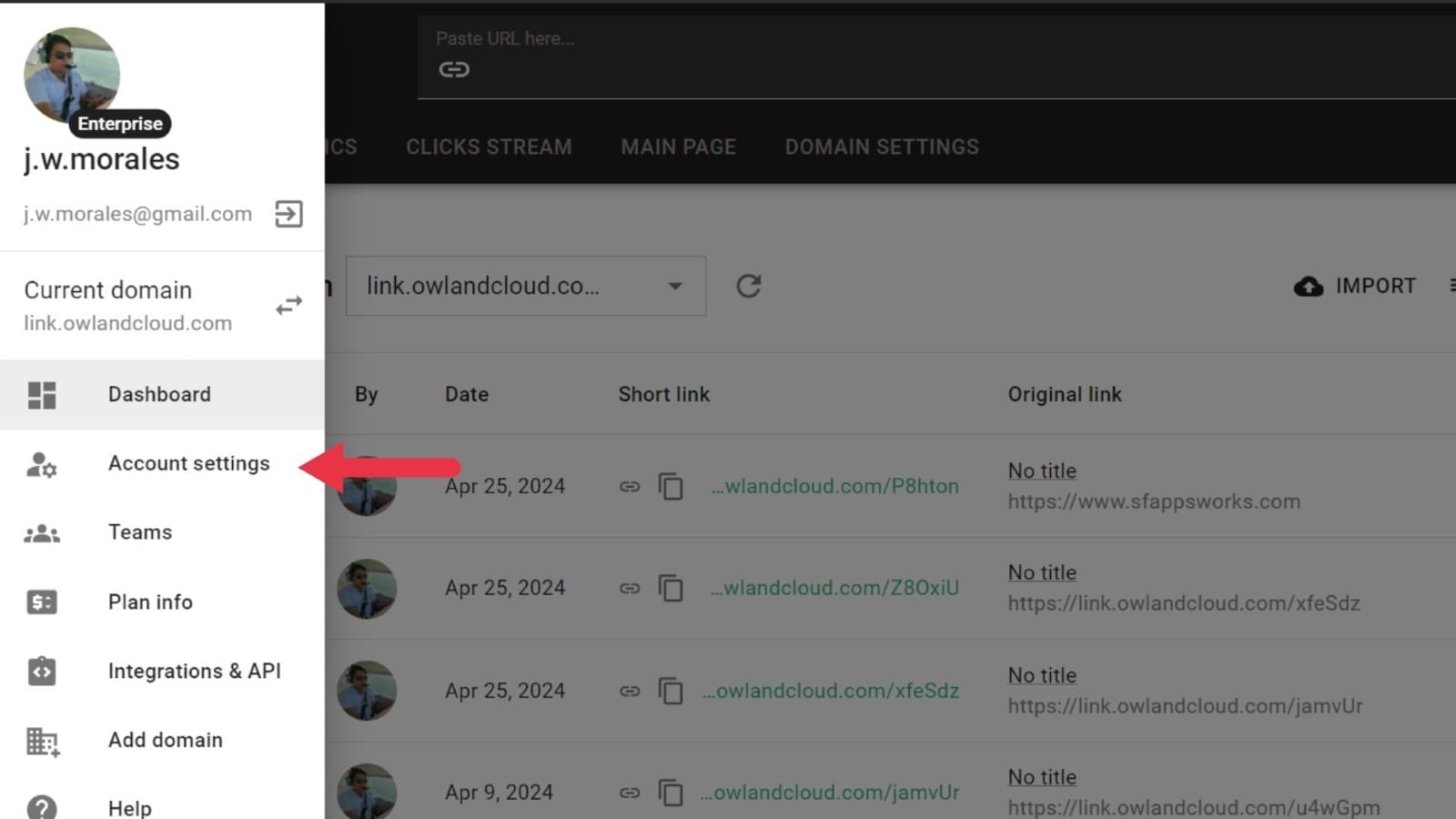
- Access Account Settings
- Click on your user avatar in the top-right corner to open the User Menu.
- Select Account Settings from the dropdown menu.
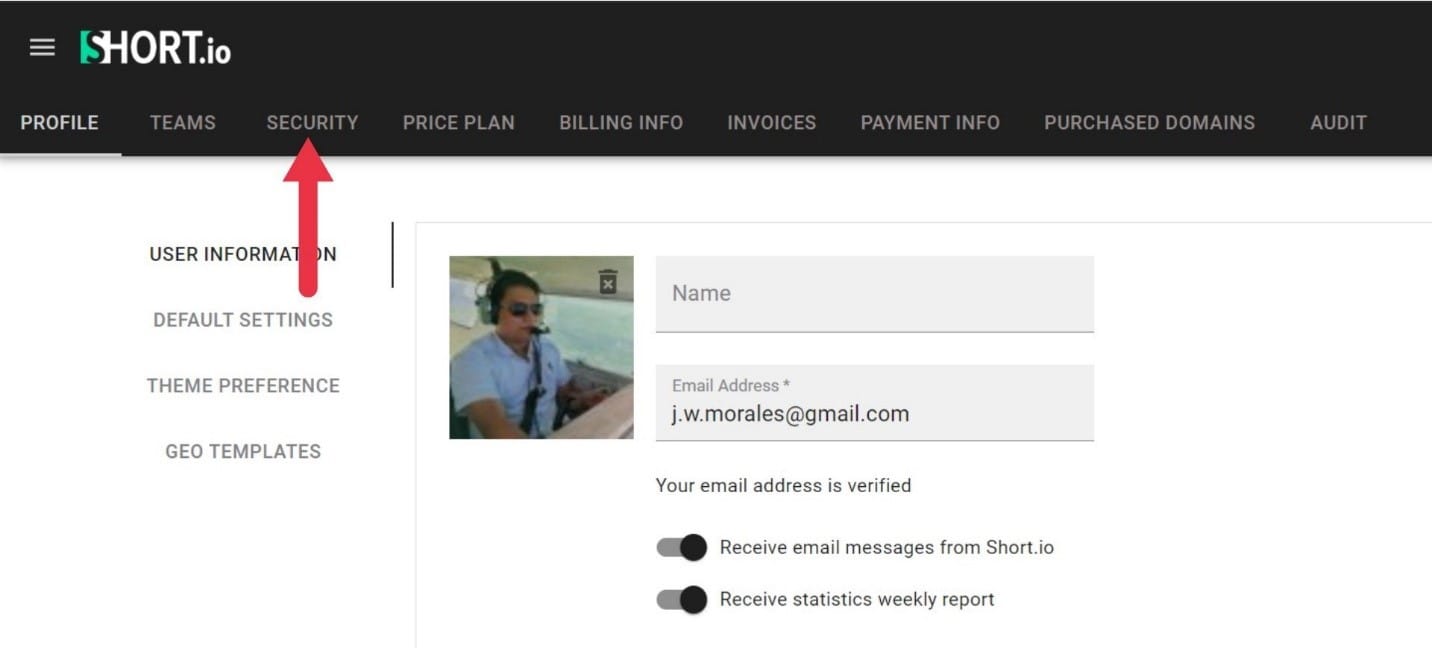
- Open the Security Tab
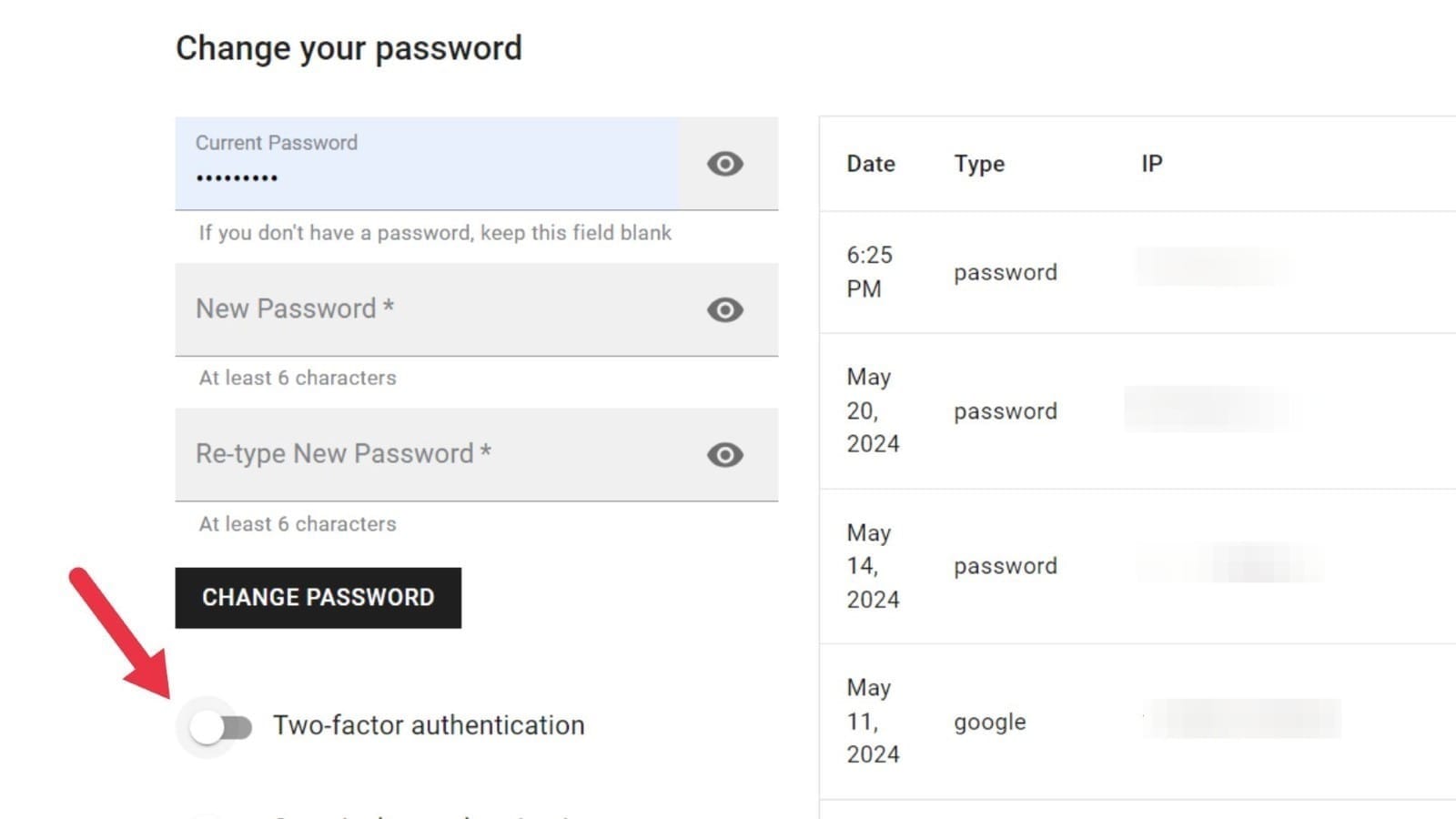
- Enable 2FA: find the Two-Factor Authentication option and toggle the switch.
- Download and set up your authenticator app. We recommend using Google Authenticator, which is available on iOS and Android.
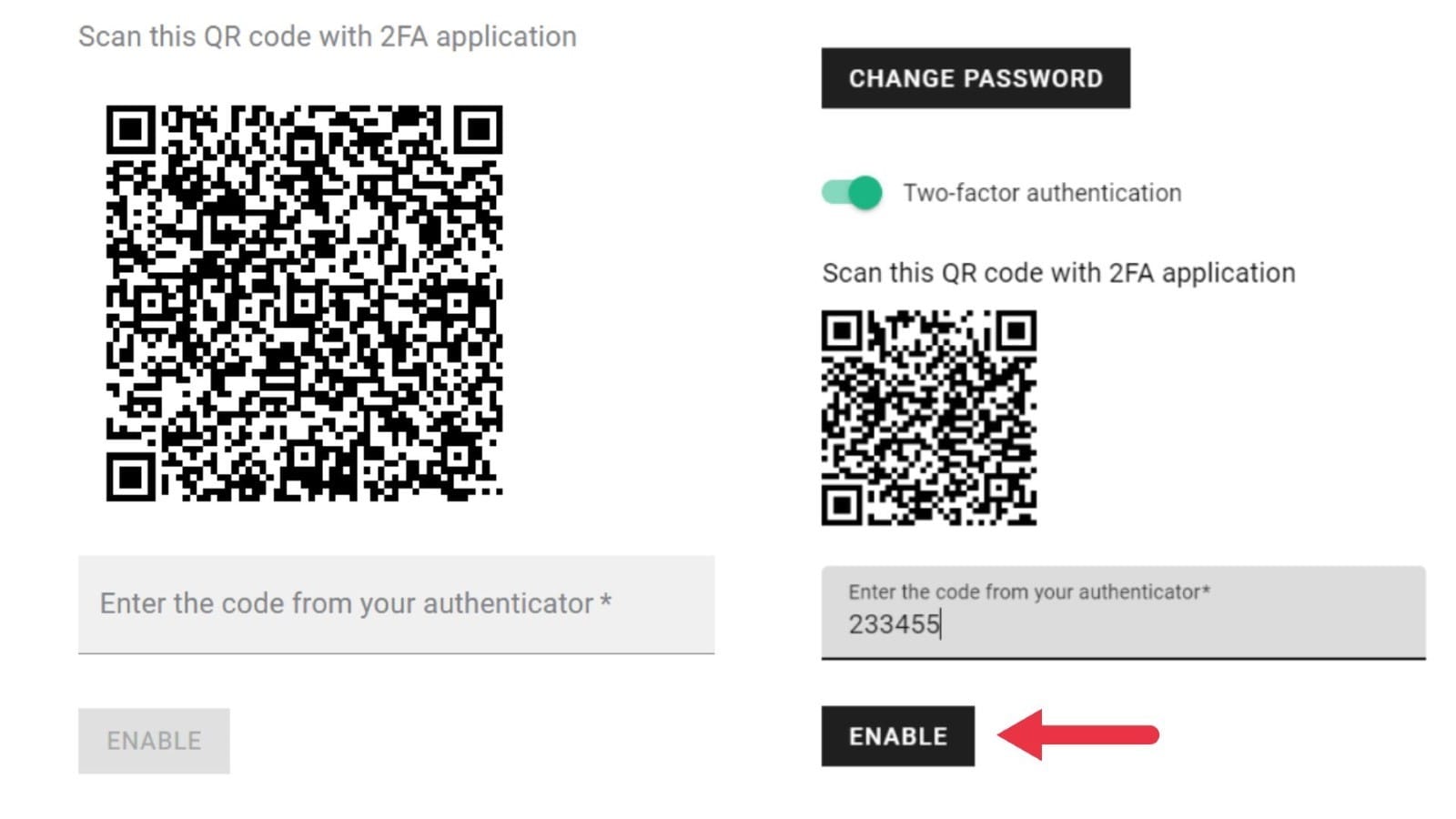
- Scan the QR Code
- To link to your Short.io account, open the authenticator app on your phone and select 'Scan QR Code'. From there, you can scan the code displayed on the Short.io Security tab.
- Enter the Verification Code
- Your authenticator will display a six-digit code that changes every 30 seconds. Enter this code into the verification field on Short.io and click Enable.
Tips for Success:
- Backup Codes: After enabling 2FA, save any backup codes provided by Short.io. These codes can be used to access your account if you lose access to your authenticator app.
- Secure Your Device: Ensure that your mobile device is secure. Use a strong password or biometric lock.
- Regular Updates: Keep your authenticator app and Short.io account details updated to avoid security issues.
By following these steps, you enhance the security of your Short.io account, protecting it against unauthorized access.
What Is 2FA?

Two-factor authentication (2FA) is a user verification process in which you need to use two different methods to gain access to an account. This helps secure an account by requiring another authentication method aside from the password, meaning attackers need to breach another device (aside from the username and password combination) to gain access to an account.
The correct username and password combination is usually the primary authentication method. The secondary factor in 2FA is then a software or hardware token that generates or receives a one-time verification code that expires within a set time period. These two indicators reduce the risk of unauthorized access, even if one factor (typically the password) becomes compromised.
Benefits of 2FA
2FA addresses the weaknesses of traditional password-based security by adding an extra layer of protection. Below, we explore the key benefits of implementing 2FA.
Addressing the Vulnerabilities of Password-Based Authentication

Passwords are often the weakest link in cybersecurity. They can be stolen through phishing attacks, where users are tricked into providing their passwords to malicious entities. Brute-force attacks, on the other hand, involve the use of automated tools to crack passwords.
Data breaches at service providers can also expose passwords, putting users at risk. Even complex passwords can be insufficient to protect sensitive accounts. With advanced techniques, attackers can eventually break through security protocols.
Additionally, many users reuse passwords across multiple sites, compounding the risk if one password is compromised.
Enhanced Security Through Multi-Factor Authentication

2FA adds a second layer of security that is independent of the password. Even if an attacker manages to steal your password, they will still need access to your second factor--typically a smartphone or a hardware token, to enter your account.
Multiple verification factors make it exponentially more difficult for attackers to access your accounts. They would need to compromise both your password and secondary factor, which is a much more complex and less likely scenario than just guessing or stealing a password.
Protection Against Credential Theft

In environments where Bring Your Own Device (BYOD) policies are prevalent, 2FA provides a robust security measure that does not rely solely on company-provided hardware. Employees can use their personal devices for the second factor, enhancing security without additional costs.
2FA can significantly mitigate the risks associated with stolen or compromised passwords. Even if attackers obtain your password, they cannot access your account without the second factor, thereby preventing account takeovers.
2FA ensures that even if your password is compromised through a phishing attack or data breach, your account remains secure. Unauthorized users will be unable to bypass the second authentication step.
Safeguarding Personal and Sensitive Information

By requiring two forms of verification, 2FA helps protect your data, financial information, and confidential documents from unauthorized access. This level of security is crucial for both individuals and organizations that handle sensitive information.
With 2FA in place, the impact of security breaches is minimized. Even if passwords are exposed during a breach, the additional layer of security provided by 2FA ensures that accounts remain protected, reducing the potential damage.
User Confidence and Trust
Users are more likely to trust a service that offers robust security measures like 2FA. Knowing that their accounts are well-protected increases user confidence and satisfaction. Implementing 2FA reassures users that their sensitive information is adequately protected, fostering a sense of security and trust in the service provider.
Adapt to the Evolving Threat Landscape
The cybersecurity environment is always changing, with new threats appearing frequently. 2FA is a proactive measure that helps you stay ahead of these threats by providing an additional layer of defense. Short.io not only offers robust 2FA capabilities but also integrates seamlessly with other essential tools for secure online navigation.
By enabling 2FA on your Short.io account, you significantly enhance your digital security, safeguarding your information and boosting user confidence. In today's threat landscape, Short.io's comprehensive security features ensure your information stays protected and secure.

