Cybersecurity is a critical concern for organizations, especially with the increasing reliance on online platforms for collaboration and communication.
One effective measure to enhance cybersecurity is implementing two-factor authentication (2FA) on your corporate platforms. This method requires users to provide two different authentication factors to verify their identity, adding an extra layer of security beyond the standard password-only approach.
How to Enforce 2FA for Team Members
Implementing 2FA for your organization doesn't have to be daunting—it mostly depends on the link shortener you’re using. In Short.io, enforcing 2FA for team members is a seamless process. Here's a handy guide on enabling 2FA for your Short.io account.
Once you’ve done that, activating 2FA for your team members requires these additional steps:
- Click the Menu icon on the top right corner of your dashboard.
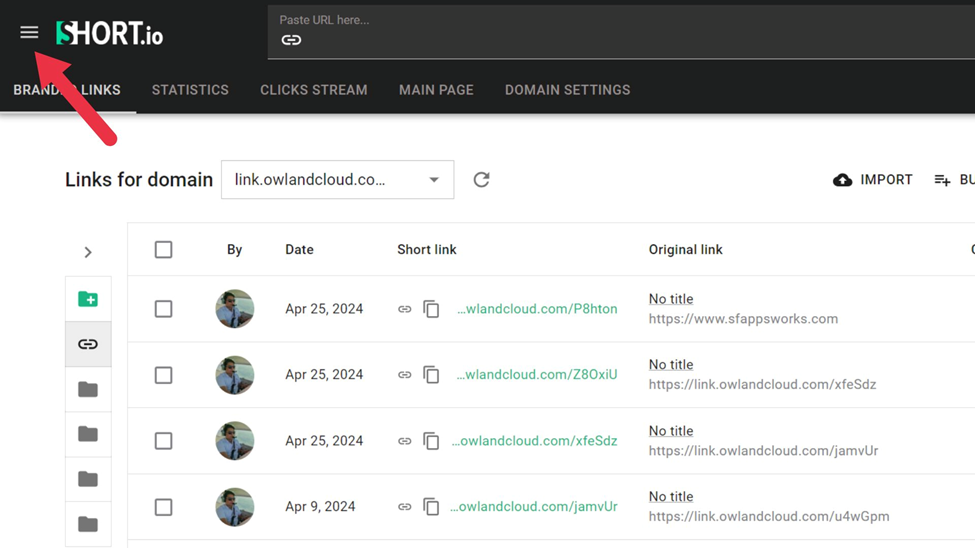
- Click Teams.
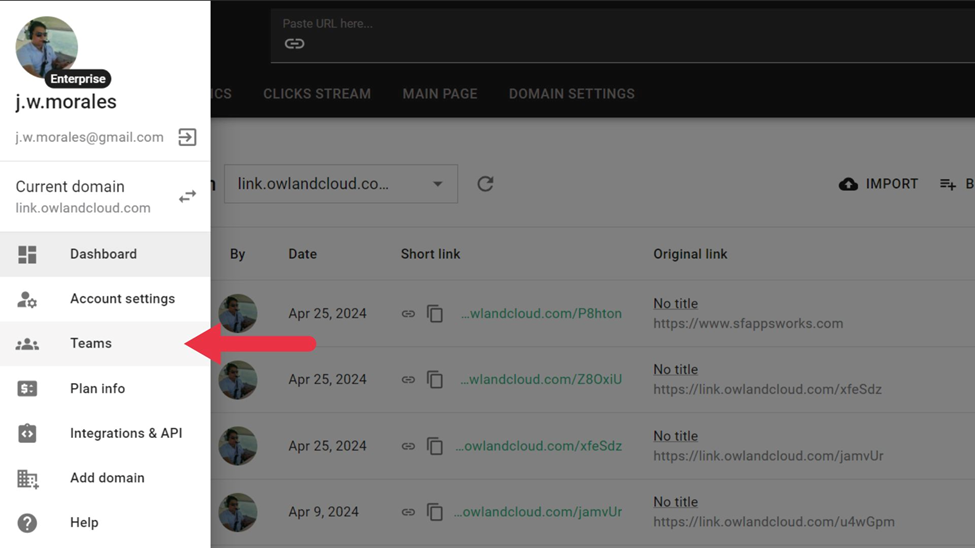
- Click Enforce 2FA.
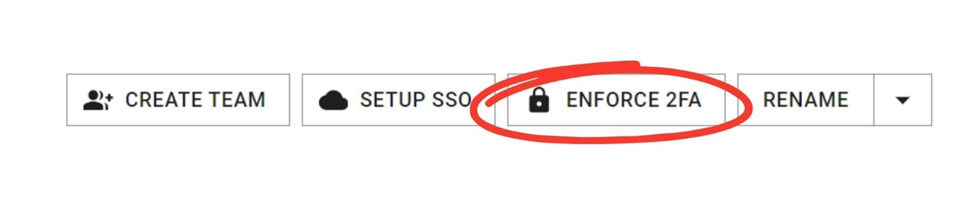
- When the pop-up window comes, click Confirm.
With those four easy steps, you increase the security of your entire team by enforcing two-factor authentication on every member.
Why Your Team Needs 2FA
2FA offers advantages that address common security challenges at a corporate level. Let's explore why implementing 2FA across your team accounts is a game-changer for your organization.
Enhanced Security for Team Collaboration

Imagine your team's communication as a fortress. Your password is the gate, but it's vulnerable to attack without a vigilant guard. 2FA is that guard, making unauthorized access to team accounts significantly more challenging for cyber criminals.
Unauthorized access can lead to severe consequences, including data breaches, loss of sensitive information, and compromised communication channels. By requiring two forms of authentication, 2FA makes it substantially more difficult for attackers to access team accounts, even if they manage to obtain a user's password.
Bad actors gain unauthorized access from weak passwords, phishing attacks, or data breaches. An attacker can steal sensitive information, disrupt operations, and damage an organization's reputation.
Control Over Access Levels

Implementing 2FA in conjunction with RBAC gives organizations more granular control over who can access what information and perform which functions within their systems. This combination ensures that users only have access to the data and tools necessary for their roles, minimizing the risk of unauthorized access.
RBAC allows administrators to assign permissions based on users' organizational roles. When this works together with 2FA, attackers cannot easily access sensitive areas even if credentials are compromised.
For example, an IT department can use RBAC to restrict access to a system's administrative functions to only a few senior members, while all users must use 2FA to log in. By using 2FA and RBAC together, organizations can limit the potential damage of a security breach.
Sensitive data and administrative functions are only accessible to those who actually need them, and the additional layer of security provided by 2FA makes unauthorized access attempts much more difficult.
Facilitation of Remote Work and BYOD Policies

Remote work and BYOD (Bring Your Own Device) policies are becoming the norm. But with great flexibility comes great responsibility. 2FA is crucial in enabling these modern work arrangements without compromising security.
Remote work often involves accessing company systems from different locations, sometimes using public or unsecured networks. 2FA provides an extra layer of security, ensuring that the accounts remain protected even if the network is compromised.
For example, employees working from home can securely access company resources using a combination of passwords and authentication apps or hardware tokens. BYOD policies allow employees to use their devices for work, increasing convenience and productivity.
However, personal devices may not have the same level of security as company-issued hardware. Implementing 2FA helps mitigate this risk by ensuring that access to sensitive information requires more than just a password.
Prevention of Account Takeovers and Phishing Attacks

Cybercriminals are getting craftier, and their weapons of choice are account takeovers and phishing attacks. But 2FA is like a superhero cape for your security. It significantly reduces the likelihood of these attacks succeeding.
Even if attackers can obtain a user's password through phishing or other means, they still need the second authentication factor to access the account, making it much harder for them to crack the accounts.
Phishing attacks often trick users into revealing their passwords by pretending to be a legitimate source. With 2FA, the attacker cannot access the account without the second authentication factor, even if the password is compromised.
Adaptation to Dynamic Team Environments

Organizations constantly change. Your security measures need to be just as dynamic. 2FA solutions can scale and adapt to these changes, ensuring that security measures remain effective regardless of the organizational dynamics.
2FA can quickly scale to accommodate new members and roles as teams grow or restructure. For example, when a startup expands rapidly and hires new employees, 2FA can be quickly deployed to secure the accounts of all new team members. This scalability ensures that every new employee starts with the same level of security, maintaining a consistent security posture across the organization.
Additionally, 2FA can adapt to changing roles and responsibilities as team structures evolve. When employees are promoted or shift roles, their access requirements change. 2FA can be adjusted to reflect these new access needs, ensuring that security measures remain robust and appropriate. This adaptability helps maintain a secure working environment ready to meet the challenges of today’s dynamic business landscape.
Short.io Can Do More
Short.io can help you tighten your team’s security, but that’s just the tip of the iceberg. With the right plan, powerful features like A/B Testing, Geotargeting, Deep Links, etc. become available. Check out Short.io now and see how its arsenal of tools can help your online projects grow.

